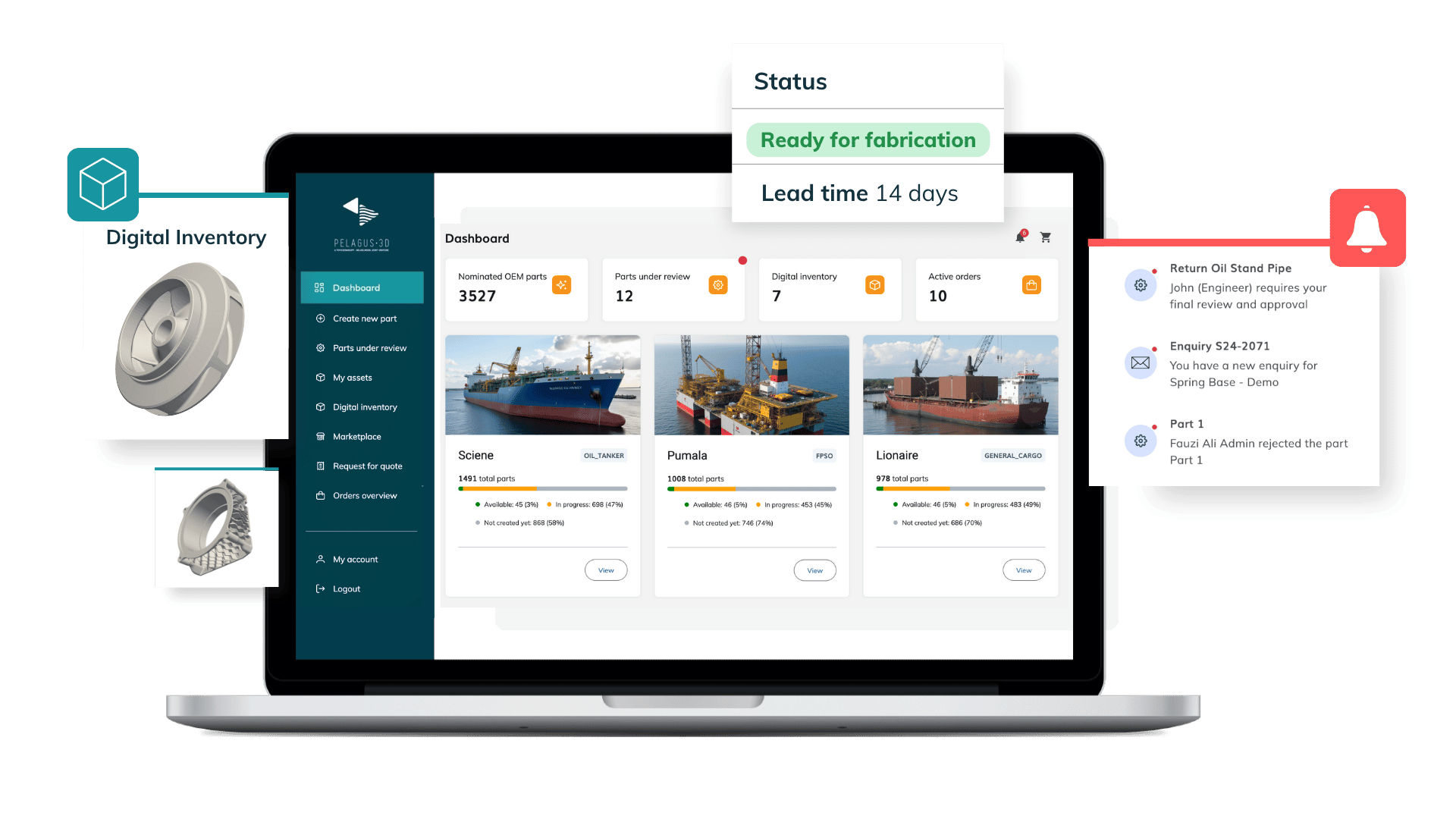
-
All fabricators are carefully vetted, onboarded and under NDA
-
IP owner identity not revealed to the fabricators
- NDA covers technical data, designs, schematics and all other forms of intellectual property
protection at every step
We enable secure, compliant on-demand manufacturing without compromising control of OEM part data.
.jpg)
End to End IP Protection for OEM Data
.png?width=300&name=Threat%20(1).png)
Risk

Safeguard
Initial Discussion
Disclosure of sensitive information
NDA & Code of Conduct - bound team, controlled information flow.
Data Collection
Unsecured channels (email, shared drives) could expose IP.
Encrypted data channels and upload via secure Pelagus Platform. Access-controlled.
Digitization & File Creation
Data exposed during processing and internal handling.
NDA-bound team, Platform cybersecurity, access control, controlled information flow.
File Storage
Unauthorized access or data breach
Enterprise-grade storage (Microsoft Azure) Platform Cyber Security, ISO 27001 certified infrastructure (Information Security Management System), full access logs.
Supplier Selection from Pelagus Network
IP misuse or supplier bypassing the OEM
Vetted, NDA-bound suppliers. OEM & End User identity not disclosed. Shortlist of suppliers selected based on capabilities and OEM Preferences (cost & location).
Quote / RfP > PO Approval
IP misuse or supplier bypassing the OEM
Data minimization (only anonymized geometry/manufacturing info shared). OEM and End User identity never disclosed. All suppliers pre-vetted, NDA-bound.
Fabrication
IP misuse or supplier bypassing the OEM
Only anonymized files and essential manufacturing data are shared. No OEM identity, application, or part numbers. File access control.
Quality Testing
Undisclosed third parties involved in testing
All testing is coordinated through Pelagus including 3rd party witnessing with Class / Certification bodies. We work only with reputable accredited test labs. Full traceability and documentation included.
Dispatch
Leakage of OEM / End User contact information.
Dispatch through trusted partners. All stakeholder information concealed. Chain of custody logged digitally, with traceability maintained.
Our IP Protection Measures in Detail
Authorized Personnel
- Only authorized personnel can access OEM platform account and secure files
- User identity authenticated through 2FA to access individual accounts and retrieve data
Contractual Safeguards
- Supplier & Employee NDAs: Drafted by industry experts to protect all shared data.
- Code of Conduct: Mandatory for all staff and suppliers
- Cybersecurity Training: Required for all employees
Vetted Suppliers
Pelagus 3D ISO Certifications
- Under the Integrated Management System (IMS), we have achieved International Standard certifications across our global operations.



File Handling
- Drawings, models and specification documents are anonymized
- Only essential manufacturing requirements are shared with fabricators
Cybersecurity
- Regular Penetration Testing
Independent CREST-certified firms test our platform using OWASP standards to detect and resolve vulnerabilities. - Real-Time Threat Monitoring
Cloud-native security defends against unauthorized access, DDoS attacks, and firewall breaches — with continuous monitoring. - Two-Factor Authentication (2FA)
Required for all user logins to block phishing, stolen credentials, and brute-force attempts. - Token-Based User Authentication
Ensures secure access control and session management across all platform activity. - AES-256 File Encryption
Files are encrypted automatically at rest and protected in transit with TLS — no action needed from the user.
Frequently Asked Questions
How do you control who can access our part files and data?
Access to the Pelagus platform is strictly managed through account-based permissions and two-factor authentication. Only authorized users can view or upload files, and access is never granted to third parties without OEM approval.
What prevents suppliers from re-accessing our files or data?
Files are encrypted, access is logged, and all production runs are locked to specific orders. Files and data are only shared in the duration of the fabrication job and access is closed right after.
Can any supplier in your network see our designs?
No. Files are only shared with vetted suppliers, chosen specifically for each job. The RFQ process is closed and targeted — not open to all.
Will the fabricator know who we are or what the part is for?
No. Files are anonymized before they reach suppliers. OEM identity, part number, and application context are all removed. Suppliers only see the information needed to manufacture the part to spec.
What legal safeguards are in place with your suppliers?
All suppliers sign NDAs and a Code of Conduct agreement. These cover IP handling, confidentiality, and prohibit unauthorized sharing or use of any design data.
How do you ensure your cybersecurity standards are up to date?
We conduct regular penetration testing to assess our system against the latest cyber attack techniques and emerging threat methodologies.
> Penetration tests (CREST certified)
> AES-256 encryption
> Dedicated cloud security suite
Can we be sure our files are encrypted in storage and during transfer?
Yes. All files are encrypted at rest and in transit using industry-standard TLS and AES-256 protocols.
What happens if we stop working with Pelagus — can we remove our data?
Yes. You retain full ownership of your files and can request complete data removal at any time.
How do you prevent a supplier from going around you to sell directly to the end user?
Suppliers never receive OEM identity or end-use details. Final delivery is routed through Pelagus, with full traceability and contractual controls preventing direct contact or unauthorized resale.
How do you improve your IP security over time?
We are constantly working to further anonymize and improve traceability across the entire chain.
We are constantly on the lookout for new industry best practices and tools that improve our IP security as part of our continuous improvement practice.